 We
provide an extensive range of IT security
services which include conducting security
reviews and risk assessment, developing policies
and standards, recommending and implementing
security solutions, as well as conducting
security awareness training for different levels
of staff.
We
provide an extensive range of IT security
services which include conducting security
reviews and risk assessment, developing policies
and standards, recommending and implementing
security solutions, as well as conducting
security awareness training for different levels
of staff.
Consultation and
Training
We provide and
extensive range of IT consultancy services to
help customers deal with the new challenges in
the IT and Data security arena. We firstly help
our client identify a list of system risks and
its potential impacts to the business. Then
using a series of interviews with relevant
staff, site surveys and system checks, we review
the site of enterprise for compliance with the
prevailing IT security policies, standards are
guidelines, a recommendation on appropriate
measures and compensating controls with then be
made to eradicate risks posed by
non-compliance. The network is then tested with
a suite of scanning tools to provide snapshots
of the vulnerability of the network/server. A
security policy and plan is then drawn up, and
the relevant staff members are also trained and
educated to use the system in a way that doesn’t
create security risks and keeps the network
secure.
Data Protection
This the
implementation process for the new security
system and policy. This is broken up into 5
main sections
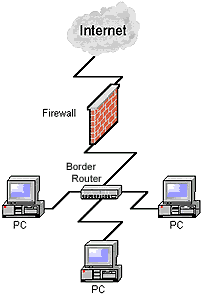
1 - Integrated
Architecture
Implementation and
management of firewalls and network perimeter
security
– We offer our clients a suite of services to
manage the entire life cycle of the network
firewalls and related security services. These
include installation, configuration,
maintenance, and continued auditing and review
of the firewalls and their rule-base.
Virtual Private
Network Infrastructure
– We help clients with remote or multiple sites
to effectively extend their network beyond
physical boundaries. Our virtual private network
infrastructure solutions provide secure logical
links among these sites.
2 - Content
Intrusion detection
-
We
assist our clients in the installation of the
intrusion detection systems, and the monitoring
of networks and hosts for any signs of an attack
or unusual behaviour
on the network. This allows appropriate
counter-measures to be taken before and serious
security breach occurs, minimizing damages.
Anti-virus and
Content Security -
We
provide enterprise-wide anti-virus solutions
that are centrally managed, reducing the
dependence on individual scanning activities on
each machine. We also offer content filtering
solutions which are capable of filtering and
quarantining online traffic that could
potentially contain viruses, based on certain
content keywords and other objects.
3 - Access
User Authentication
– We
configure and integrate authentication solutions
which enable our clients to identify their users
positively. These include enhanced versions of
the well-known User ID and Password combination,
or two-factor authentication using hardware
tokens and smartcards.
Identity Management
and Single Sign-On
systems are able to
provide a centralized view of the users and
their access across multiple sub-systems. Our
solutions encompass multi-layered authentication
and authorization services from a central
security management perspective.
Encryption and
Smartcards –
The design of the
encryption protocol and the management of the
encryption keys are critical to safeguard the
overall security of your information.
our application based
encryption solutions ensure that your critical
information remains secure across servers. Our
consultation and implementation capabilities
result in a holistic approach, creating maximum
security for your critical information
4 - Desktop
We
provide desktop security solutions encompassing
access control, encryption, patch measurement
and personal firewall to secure access to your
desktop, protect your data from disclosure and
theft, resolve system vulnerabilities and block
malicious activities. Our solutions also
facilitate the enforcement of corporate policies
at your desktops, hence ensuring that they are
secured wherever they may be and that they do
not pose a threat to your
organisation.
5 -
Application
With
consistent security being required across
multiple layers of applications and product
solutions, our
application security specialists have the
capability to help you with integrating various
security components at the application layer.
This ensures that authentication,
confidentiality, integrity and even
non-repudiation requirements are met
consistently across your applications and
infrastructure.
Management
Outsource the management and monitoring of your
security infrastructure. Our 24x7 remote and
onsite management services enable your
organisation to
focus on the core business, leaving the
management of the security infrastructure in our
safe hands. By protecting your connectivity
services with comprehensive managed firewall
services and VPN, we ensure secure data services
and reliable business connectivity to both local
and overseas organisations.